Introduction:
In this blog post, I will explain what is UEFI malware, how it works, and why it is so dangerous. I will also provide some tips on how to protect your Windows machine from this threat.
1.What is UEFI malware?
UEFI stands for Unified Extensible Firmware Interface, and it is the low-level software that bridges the device firmware with the operating system. It is responsible for booting up your computer and loading the OS kernel. UEFI malware is a type of malicious software that targets the UEFI firmware or the EFI system partition, which are stored in a flash chip on the motherboard or on the hard disk respectively. UEFI malware can hijack the boot process and load malicious code before the OS or any security software can run. This makes it very stealthy and persistent, as it can survive OS reinstallation or hard disk replacement.
2.How does UEFI malware work?
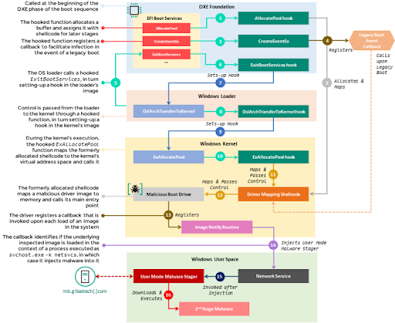
UEFI malware works by exploiting vulnerabilities in the UEFI firmware or the EFI system partition, or by tricking users into installing trojanized software that can modify these components. Once installed, UEFI malware can disable OS security mechanisms, such as Secure Boot, User Access Control (UAC), and antivirus software. It can also inject malicious code into the OS kernel or user mode, giving it full control over the system and allowing it to perform various malicious activities, such as stealing data, spying on users, encrypting files, or installing other malware.
3.Why is UEFI malware so dangerous?
UEFI malware is very dangerous because it is hard to detect and remove. Most security software cannot scan or access the UEFI firmware or the EFI system partition, as they are protected by cryptographic signatures and access control mechanisms. Even if security software can detect UEFI malware, it may not be able to remove it, as it may require flashing the firmware chip or formatting the EFI system partition, which can be risky or impossible for most users. Moreover, UEFI malware can bypass Secure Boot, which is an industry-standard that verifies the integrity of the boot process and prevents unauthorized firmware modifications. Secure Boot is supposed to create a chain of trust that ensures that only trusted firmware can run during startup. However, UEFI malware can exploit unpatched or unknown vulnerabilities in the Secure Boot process to break this chain of trust and load malicious firmware.
4.What is an example of UEFI malware?
One example of UEFI malware is BlackLotus, which was discovered by researchers in March 2023. BlackLotus is the world's first-known instance of real-world malware that can hijack a computer's boot process even when Secure Boot and other advanced protections are enabled and running on fully updated versions of Windows¹. BlackLotus is based on a hacking tool called VectorEDK, which was created by Hacking Team, a now defunct hacking-for-hire contractor based in Italy³. BlackLotus exploits a vulnerability in Windows bootloader (CVE-2022-21894) that allows it to bypass Secure Boot and install itself on the EFI system partition¹. BlackLotus was initially sold on hacker forums for as little as $5,000, giving access to malware that is often associated with state-sponsored hacking operations². However, in July 2023, the original source code of BlackLotus was leaked on GitHub, making it available to anyone who wants to use or modify it². This poses a significant threat, as it may be combined with new vulnerabilities to create new variants of UEFI malware.
5.How to protect your Windows machine from UEFI malware?
There are some steps you can take to protect your Windows machine from UEFI malware:
- Keep your firmware and OS updated with the latest patches and security updates.
- Enable Secure Boot and do not disable it unless you have a valid reason.
- Use antivirus software that can scan and protect the EFI system partition.
- Do not install software from untrusted sources or click on suspicious links or attachments.
- Use encryption tools such as BitLocker or VeraCrypt to protect your data in case of compromise.
- Monitor your system for any signs of infection, such as unusual behavior, performance issues, or network activity.
- If you suspect that your system is infected with UEFI malware, contact a professional for assistance.
UEFI malware is a serious threat that can compromise your Windows machine at the deepest level. By following these tips, you can reduce your risk of becoming a victim of this stealthy and persistent attack.
¹: [Stealthy UEFI malware bypassing Secure Boot enabled by unpatchable Windows flaw | Ars Technica](https://arstechnica.com/information-technology/2023/03/unkillable-uefi-malware-bypassing-secure-boot-enabled-by-unpatchable-windows-flaw/)
²: [This free UEFI malware code can hack Windows machine forever, even if hard disk is removed](https://www.securitynewspaper.com/2023/07/13/this-free-uefi-malware-code-can-hack-windows-machine-forever-even-if-hard-disk-is-removed/)
³: [A China-Linked Group Repurposed Hacking Team’s Stealthy Spyware](https://www.wired.com/story/hacking-team-uefi-tool-spyware/)
(1) Stealthy UEFI malware bypassing Secure Boot enabled by unpatchable .... https://arstechnica.com/information-technology/2023/03/unkillable-uefi-malware-bypassing-secure-boot-enabled-by-unpatchable-windows-flaw/.
(2) A China-Linked Group Repurposed Hacking Team’s Stealthy Spyware. https://www.wired.com/story/hacking-team-uefi-tool-spyware/.
(3) This free UEFI malware code can hack Windows machine forever, even if .... https://www.securitynewspaper.com/2023/07/13/this-free-uefi-malware-code-can-hack-windows-machine-forever-even-if-hard-disk-is-removed/.
(4) Unkillable UEFI Malware Bypassing Secure Boot Enabled By ... - Slashdot. https://it.slashdot.org/story/23/03/06/1854200/unkillable-uefi-malware-bypassing-secure-boot-enabled-by-unpatchable-windows-flaw.











0 Comments